How VpnCloud handles NATs
What is NAT?
In general, NAT ("Network address translation") is used to enable between communication between networks with incompatible address spaces by mapping addresses from one address space to another.
In the most common case, NAT is part of a consumer router (e.g. a DSL router) and translates the private addresses used inside the home network to public addresses on the normal Internet. This required since Internet providers usually only provide one IP address to their customers but they have multiple devices in their home network that access the Internet.
Customers then use private IP addresses (one per device) inside their home network and the router maps them to the one public address assigned by the provider.
How does the mapping work?
Technically, the mapping translates local IP addresses and ports numbers into different ports on the single pulbic IP address of the router. For outgoing data packets, the internal source address and port is translated into the mapped address and port. For incoming data packets, the destination address and port are replaced with the mapped internal address and port. This way, both the local device and the server on the Internet can communicate with each other and don't need to know about the NAT.
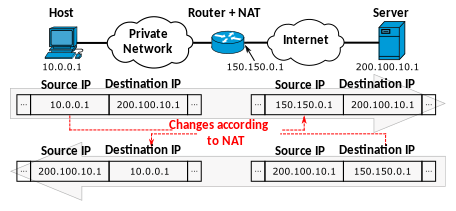
(Source: Michel Bakni, CC BY-SA 4.0, via Wikimedia Commons)
The router stores the mapping in a mapping table. When no entry is found for an outgoing packet, a random free port is chosen and assigned to the internal address and port in a new mapping entry. Incoming packets without mapping entry are just dropped since no destination is known.
After some time of inactivity, mapping table entries time out and are removed, which means that any further data for that connection from the Internet side will be dropped.
What does that mean for node connectivity?
NAT has the effect that nodes on the Internet can only reply to requests by local nodes but not not initiate connections with them. Most users regard this as a security feature which it certainly is but for peer to peer applications this creates problems.
Reachability becomes asymmetric: Nodes on the Internet can not reach nodes behind a NAT but nodes behind the NAT reach them.
The situation is even worse when two nodes are behind different NATs, they can not initiate connections to each other.
How does VpnCloud handle NATs
In order to avoid NAT timeouts, VpnCloud keeps its connections alive. VpnCloud periodically exchanges its peer list with its peers which should avoid timeouts. Also, when VpnCloud detects a local NAT, it will increase the frequency of those exchanges to be on the safe side.
Devices behind a NAT usually only know their private IP addresses which are meaningless to peers outside the NAT. In order to compensate this, nodes that detect a local NAT, will try to ask their router for the public IP address using the UPNP protocol. Other nodes will not only rely on the address reported by a peer, but will also note down the actual address that they see the peer at. This way, other nodes will receive both the internal and the public address of nodes behind the NAT and will try to connect to both. If they are on the same NAT the internal address might work, otherwise the public address can work (see next point).
To solve the asymmetric reachability of nodes behind a NAT, all peers exchange the addresses or their peers with all their other peers (peer list exchange). If both a node behind a NAT and a node on the Internet have a peer in common, they will receive each others addresses via the peer list exchange. While the node on the Internet can not initiate the connection, the node behind the NAT will establish a connection with the other node.
Hole punching
But what about two nodes that are both behind different NATs? Even if they have a peer in common and know each others address, they can both not initiate a connection because of the NATs, right? Well, here comes a technique called "hole punching".
Most NAT routers will assign the same port on the public IP for the same internal address and port regardless of the address on the Internet it is communicating with. VpnCloud uses the same local port for all its communication, so this will result in the same external address and port seen by all its peers.
If the two nodes behind NATs, know each others external address and port (from a common peer via the peer list exchange) they can both try to send packets to each other. Even if the NAT keeps a list of allowed external addresses per mapping entry, this first outgoing packet will add the other node to that list and the next packet from that node will reach this node.
